Website Vulnerability Scanner
Technical details
What is a Website Vulnerability Scanner?
A web vulnerability scanner is a website security testing tool that automatically detects security holes and misconfigurations in web apps and their components. Its language-independent capabilities make it an essential tool for detecting common vulnerabilities in web services, web servers, proxy servers, and web application servers.
Our team developed the Website Vulnerability Scanner on Pentest-Tools.com to provide security specialists with a reliable, full-fledged solution that offers both in-depth testing options and additional automation and reporting capabilities.
What makes our Website Vulnerability Scanner different
You can use our Website Vulnerability Scanner online, without spending time on manual configuration scripts. The list of tests it performs is public and the customization options put you in full control of its functionality.
Along with its strong reporting capabilities and powerful automation features, our Website Vulnerability Scanner is a powerful tool for dynamic application security testing (DAST) and static application security testing (SAST).
Customers also integrate our website scanner into their secure software development life cycle (SDLC) process, especially through our API, and also through scheduled and bulk scans.
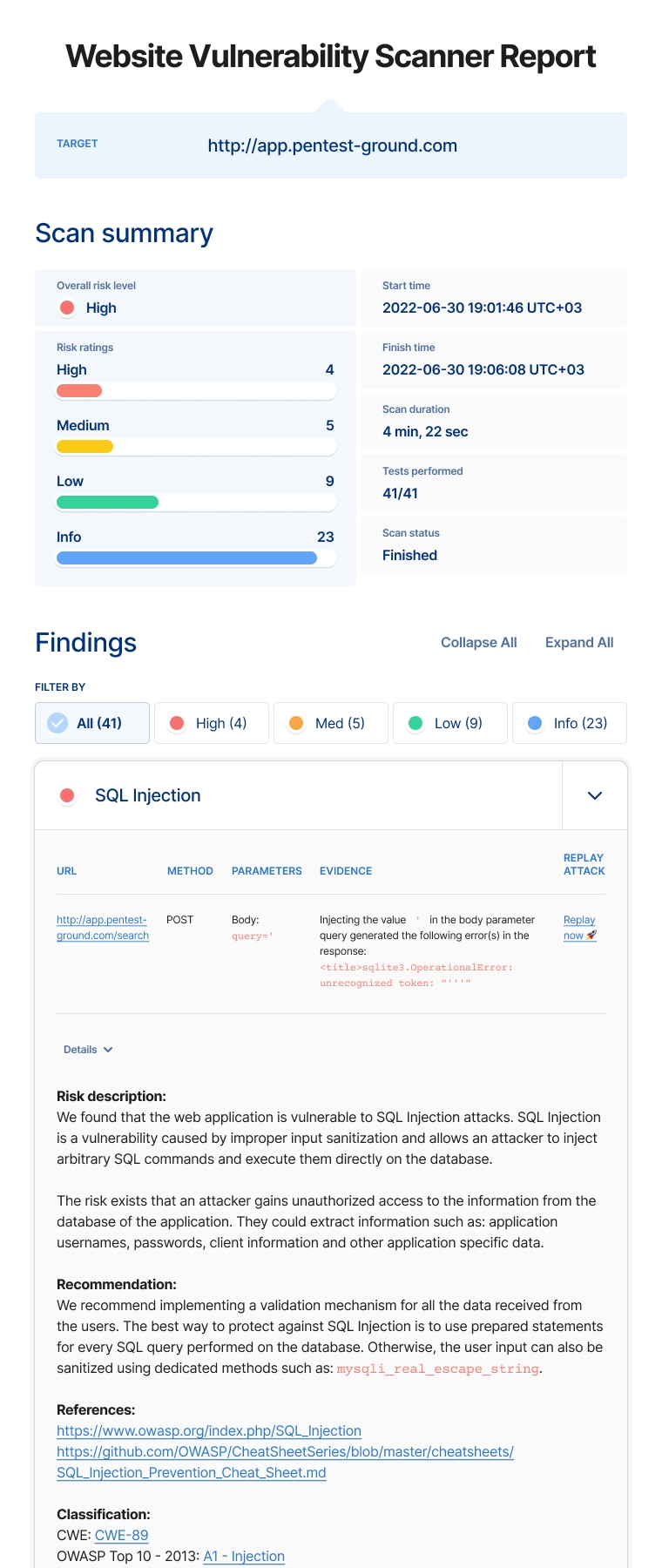
Website Scanner findings which our scanner automatically validated are marked with the Confirmed tag. Results also include screenshots and scan statistics such as URLs spidered, the total number of HTTP requests, error count, and more helpful details.
How our Website Vulnerability Scanner works
When using a website vulnerability scanner online, the goal is to push as many routine tasks to the background as possible. You can use our Website Vulnerability Scanner standalone or to dig deeper into subdomains and virtual hosts, along with open ports the TCP Port scanner and UDP Port scan tool discovered during the reconnaissance stage.
Whatever tactic you prefer, this tool helps you minimize routine tasks and gain time to use your unique expertise to make connections only a skilled specialist can.
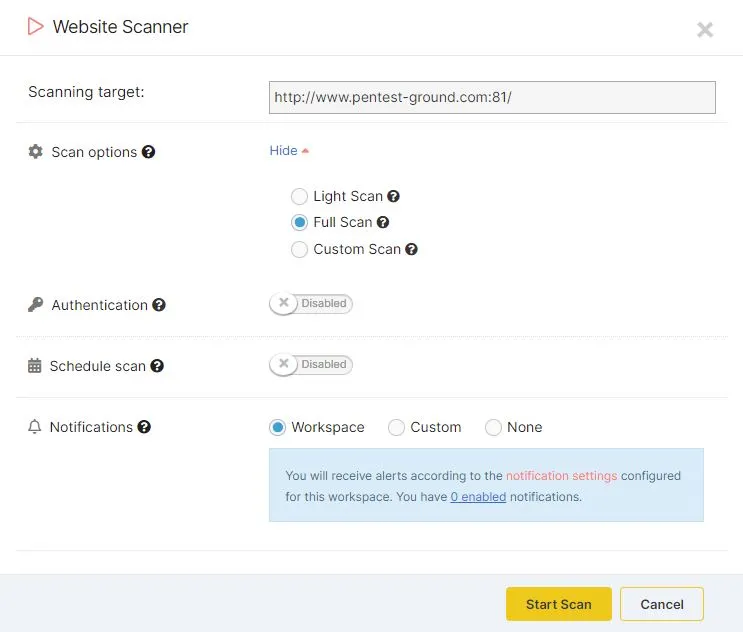
The Light Scan version – optimized for speed
You can use our tool as a free website vulnerability scanner without creating an account. This passive scan performs only a selection of legitimate requests against the target system and generates a maximum of 20 HTTP requests to the server.
Use the Light Scan if you don’t want to raise any alarms, but remember it only scratches the surface in terms of security testing.
The Full Scan version – proprietary detection
The Full scan goes into detail and attempts to map the entire attack surface of the target system by crawling the application, discovering hidden files, using more attack vectors to check for server configuration issues and outdated services, taking screenshots, and more.
This website security scan sends up to 10,000 HTTP requests, which may trigger alarms from IDS (Intrusion Detection System) devices. Not to worry though: this is not a destructive scan.
After it crawls the target application, the tool sends various inputs to the parameters of the pages and looks for specific web vulnerabilities such as: SQL Injection, Cross-Site Scripting, Local File Inclusion, OS Command Injection, and many more. The site security scanner also attempts to detect sensitive files from the server (e.g. backup files, old files, admin interfaces, archive files, etc.).
To minimize the number of false positives, the Website Vulnerability Scanner also incorporates a method for detecting 404 pages.
Rich customization options
Behind its simple interface, our Website Vulnerability Scanner hides a robust pre-configured and fine-tuned engine that runs in a distributed environment and that can perform multiple parallel scans.
To make each website security check count, combine scanning options for meticulous assessments. Customization options include the ability to:
- set custom limits for the number of requests/second made to the target
- choose from a strong list of initial tests that includes detection for HTTP Debug Methods and CORS misconfigurations
- select the spidering approach that suits your needs, including spidering depth and excluded URLs
- pick from a list of active and passive checks that incorporate detection for Log4Shell, PHP Code Injection, Python Code Injection, Perl Code Injection, Ruby Code Injection, Server-side template injection (SSTI), Broken Authentication, Mixed Encryptions Content, and many more.
Use this website scanner online with other features in our cloud platform to further boost its capabilities:
- Automation options such as pentest robots and scan templates
- Webhooks for real-time notifications
- Scheduled scans and bulk scanning
- Workspace & items sharing for effective collaboration
- Finding templates and report templates
The security scanner also gets updates on a regular basis, consistently growing stronger with new features.
Authenticated scanning
The Website Vulnerability Scanner on Pentest-Tools.com also allows you to scan the target web application as an authenticated user. You can configure authentication in several ways:
- User/Password Authentication, where the scanner first tries to authenticate to the provided login URL and get a valid session cookie. This cookie is used with all the HTTP requests done to the server, performing an authenticated scan. All you have to do is check if the authentication was successful before actually starting the scan.
- Cookie Authentication, where you can specify an already valid session cookie (or multiple ones) that get sent with each HTTP request to the server. You have to first get the session cookie by manually logging into your target application with a web browser and copy/pasting the cookie from the browser to the scanner.
- Headers Authentication, where you can specify custom HTTP headers that get sent with each request to the target application. You can use them for authentication (e.g. JWT tokens, Basic Authentication, etc.) or for other specific application functionality.
- Recorded Authentication, where you can record the steps required to authenticate into the target. The scanner then uses this recording to automatically replay the actions to obtain a valid session every time it detects that logging in again is required.

Full list of Website Vulnerability Scanner tests
| Light Scan | Full Scan | Tests performed |
|---|---|---|
| Included | Included | Fingerprint web server software |
| Included | Included | Analyze HTTP headers for security misconfiguration |
| Included | Included | Check the security of HTTP cookies |
| Included | Included | Check the SSL certificate of the server |
| Included | Included | Check if the server software is affected by known vulnerabilities |
| Included | Included | Analyze robots.txt for interesting URLs |
| Included | Included | Check whether a client access file exists, and if it contains a wildcard entry (clientaccesspolicy.xml, crossdomain.xml) |
| Included | Included | Discover server configuration problems such as Directory Listing |
| Included | Included | Check if HTTP TRACK/TRACE methods are enabled |
| Included | Included | Check if security.txt is missing on the server |
| Included | Included | Check if CORS is misconfigured |
| Not included | Included | Crawl website |
| Not included | Included | Check for SQL Injection |
| Not included | Included | Check for Cross-Site Scripting |
| Not included | Included | Check for Local File Inclusion and Remote File Inclusion |
| Not included | Included | Check for OS Command Injection |
| Not included | Included | Check for ASP Cookieless Cross-Site Scripting |
| Not included | Included | Check for Server Side Request Forgery |
| Not included | Included | Check for Open Redirect |
| Not included | Included | Check for Broken Authentication |
| Not included | Included | Check for PHP Code Injection |
| Not included | Included | Check for JavaScript Code Injection |
| Not included | Included | Check for Ruby Code Injection |
| Not included | Included | Check for Python Code Injection |
| Not included | Included | Check for Perl Code Injection |
| Not included | Included | Check for Log4j Remote Code Execution |
| Not included | Included | Check for Server-Side Template Injection |
| Not included | Included | Check for ViewState Remote Code Execution |
| Not included | Included | Check for Client-Side Prototype Pollution |
| Not included | Included | Check for Exposed Backup Files |
| Not included | Included | Check for Request URL Override |
| Not included | Included | Check for Client-Side Template Injection |
| Not included | Included | Check for HTTP/1.1 Request Smuggling |
| Not included | Included | Check for outdated JavaScript libraries |
| Not included | Included | Find administrative pages |
| Not included | Included | Check for sensitive files (archives, backups, certificates, key stores) based on hostname and some common words |
| Not included | Included | Attempt to find interesting files / functionality |
| Not included | Included | Check for information disclosure issues |
| Not included | Included | Weak Password Submission Method |
| Not included | Included | Clear Text Submission of Credentials |
| Not included | Included | Verify Domain Sources |
| Not included | Included | Check for commented code/debug messages |
| Not included | Included | Find Login Interfaces |
| Not included | Included | Sensitive Data Crawl |
Warning
Scanning parameters for paying customers
| Parameter | Description |
|---|---|
| Target URL | This is the URL of the website that will be scanned. The tool does not follow any redirects, so the exact URL will be scanned. If you want to scan only a certain directory or path, you can add it in the URL like: http://www.mycompany.com/base_directory. All URLs must start with http or https. |
| Light Scan | This is a fast, passive and non-intrusive scan. |
| Full Scan | This is a complete assessment which covers a much broader range of security tests. |
| Initial tests | Fingerprint Website, Server Software Vulnerabilities, Robots.txt, JavaScript libraries, SSL/TLS Certificates, Client access policies, HTTP Debug Methods, Security.txt file missing, CORS Misconfiguration, Resource Discovery |
| Engine options |
|
| Attack options |
|
| Authentication |
|
| Notifications | Get notifications when the scan results match the conditions you set. |
Learn how to configure the Website Scanner for best results.
What to do after running the Website Vulnerability Scanner
Besides the Website Vulnerability Scanner, you have a full arsenal of online website security testing tools on Pentest-Tools.com to carry out a thorough and effective website vulnerability assessment.
You can use the Subdomains Finder and the dedicated tools to Find Virtual Hosts for each web application. Running the TCP Port scanner and UDP Port scan tool will help you discover all open ports to achieve full coverage during your security evaluation.
Digging deeper, our various web CMS scanners help you uncover Wordpress, Drupal, Joomla, and SharePoint vulnerabilities. And you can further explore all of these with the URL Fuzzer and Password Auditor tools.
To save even more precious time, try out our ready-to-use scan templates and pentest robots which group multiple tools in one bundle, so you can launch them all at once. Both templates and pentest robots are customizable and offer the possibility to build your own reusable ones.