Network Vulnerability Scanner
Technical details
What is a Network Vulnerability Scanner?
The network perimeter of a company is the "wall" that secures internal network assets from the outside world. Connecting from outside means accessing internal assets (e.g. a company's website). This way, the network perimeter exposes important network services such as FTP, VPN, DNS, HTTP, and more.
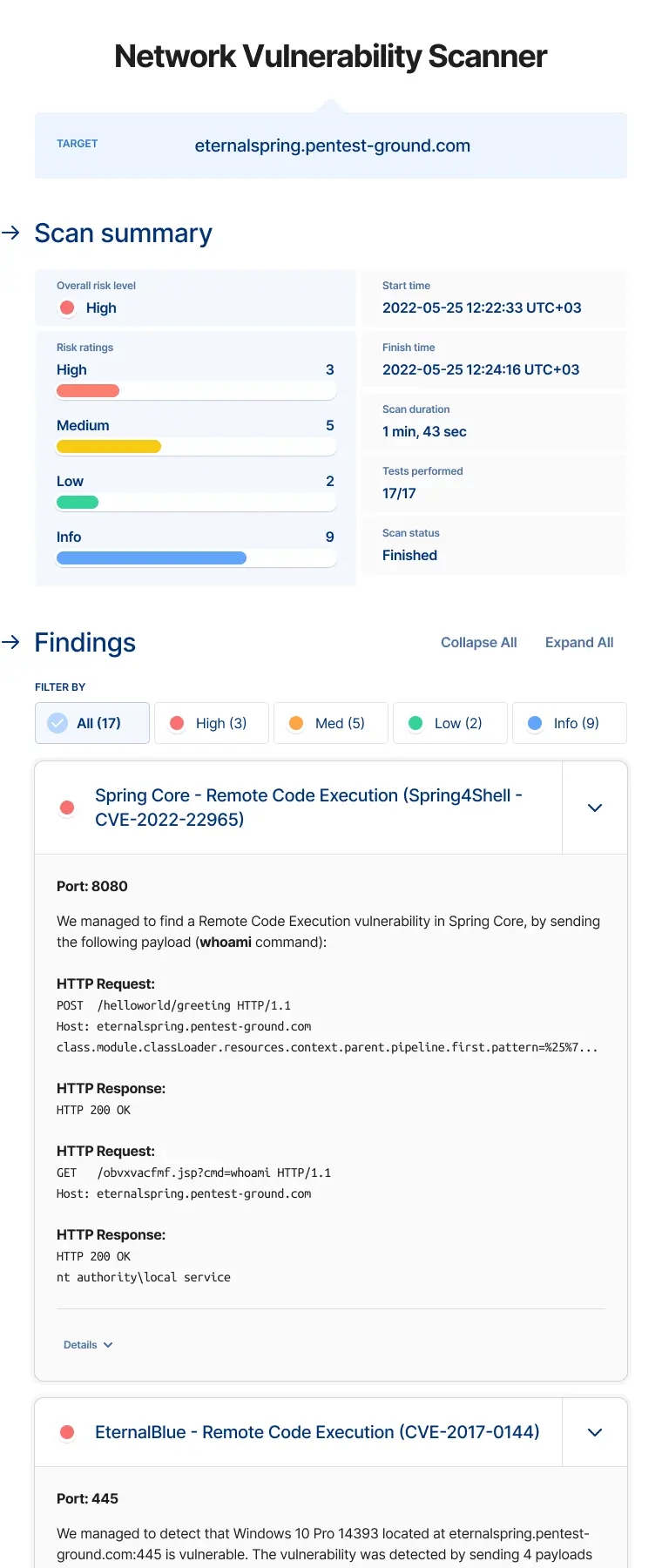
A Network Vulnerability Scanner maps all the services exposed on the network perimeter and checks for potential vulnerabilities.
What makes our Network Vulnerability Scanner different
By default, every scan begins with the host discovery phase, which employs the check alive (if enabled) and port discovery features. At Pentest-Tools.com, we run the check alive mechanism by using a customized version of Nmap's host discovery functionality which sends different types of packets called probes.
If the target is found alive, the port discovery phase scans for open ports and relevant information about them, such as running services, and continues the scan based on the results and on the type of scan you selected.
The Light Scan version – optimized for speed
The free Light version of our Network Vulnerability Scanner performs a very fast network security scan with minimal interaction with the target system.
Based on the results the discovery phase returned, our Network Vulnerability Scanner interrogates a database with known vulnerabilities to check if the specific versions of the services are affected by any cybersecurity issues. Although this detection method is faster, it can return false positives as it relies only on the version reported by the services (which may be inaccurate).
The Full Scan version – proprietary detection combined with OpenVAS
The Full version of the Network Vulnerability Scanner uses a mix of custom Sniper modules for detecting high risk vulnerabilities and the well-known OpenVAS (the most advanced open source vulnerability scanner) as a scanning engine.
It actively detects thousands of vulnerabilities in network services such as SMTP, DNS, VPN, SSH, RDP, VNC, HTTP, and many more. OpenVAS does vulnerability detection by connecting to each network service and sending crafted packets to make them respond in certain ways. Depending on the response, the scanner reports the service as vulnerable or not.
We have pre-configured and fine-tuned OpenVAS on our servers and have also added a very simple interface on top of its complex functionalities. The engine is running in a distributed environment and it can perform multiple parallel scans.
Other options in our cloud platform that boost this tool’s capabilities to detect security vulnerabilities include:
- Automatic Attack Surface mapping
- Webhooks for real-time notifications
- API access for ready-to-use scan engines
- Scheduled scans and bulk scanning
- Automation options such as pentest robots
- Workspace & items sharing for effective collaboration.
Sniper detection modules built into our Network Vulnerability Scanner
Sniper modules are custom vulnerability checks developed by our research team. They sit on top of the standard OpenVAS scan to provide quick and accurate detection for most critical vulnerabilities in high-profile software.
| name | cve | tool | updated | severity | vuln_cvssv3 | Exploitable with Sniper |
|---|
You can click here to browse the complete database of vulnerability detections and exploitable vulnerabilities.
OpenVAS scanning capabilities
OpenVAS is a fork of the old Nessus scanner, created in 2005 when Nessus became a commercial product. OpenVAS is currently developed and maintained by Greenbone Networks with support from the community.
OpenVAS implements each test in a plugin called NVT (Network Vulnerability Test). It has more than 57000 active plugins to detect a large number of vulnerabilities for many services and applications.
For example, here is how a simple NVT looks like. It's called fortigate_detect.nasl and shows if the target device is a Fortigate Firewall:
#
# This script was written by David Maciejak
# This script is released under the GNU GPL v2
#
if(description)
{
script_id(17367);
script_name("Fortinet Fortigate console management detection");
script_family("General");
script_dependencies("http_version.nasl");
script_require_ports(443);
exit(0);
}
#
# The script code starts here
#
include("http_func.inc");
function https_get(port, request)
{
if(get_port_state(port))
{
soc = open_sock_tcp(port, transport:ENCAPS_SSLv23);
if(soc)
{
send(socket:soc, data:string(request,"
"));
result = http_recv(socket:soc);
close(soc);
return(result);
}
}
}
port = 443;
if(get_port_state(port))
{
req1 = http_get(item:"/system/console?version=1.5", port:port);
req = https_get(request:req1, port:port);
<title>Fortigate Console Access</title>
if("Fortigate Console Access" >< req)
{
security_note(port);
}
}Sniper modules detection capacity
We started to develop custom detection modules in-house because OpenVAS plugins have limited coverage for vulnerabilities in commercial software. So our detection covers weaknesses in software developed by Microsoft, VMware, Oracle, F5, Cisco, MobileIron, and many more.
Sniper detection modules work by sending crafted data to the target system in order to trigger abnormal behavior. We qualify the system as vulnerable only after obtaining solid proof for it (e.g. after having extracted minimal data such as the current username, a system file, etc). A benefit to this method is that Sniper modules have a very low false positive rate.
Since OpenVAS plugins are mostly focused on open-source software, they do not overlap nor conflict with our proprietary Sniper modules. On the contrary, you can amplify the Network Vulnerability Scanner’s functionality with Sniper Auto-Exploiter: you can further exploit each detected vulnerability automatically by clicking the “Exploit with Sniper” button in the Findings section.
Open ports detection efficiency
Through our Network Vulnerability Scanner, we've configured a custom discovery phase to scan for a default list of ports, including the most common 6000 ports (TCP and UDP). However, keep in mind that, by default, the scanner first attempts to detect if the host is alive before doing the port scan.
If the host is not alive (e.g. does not respond to our probing methods), you will get a finding containing the “Host is down” message and the scan will finish. However, if the target is alive, the scanner will further search for open ports and their associated services.
Note: If the scanner does not find any open ports even though you know there are some and the host is alive, we recommend you expand the port range and re-run the scan.

Scanning parameters for paying customers
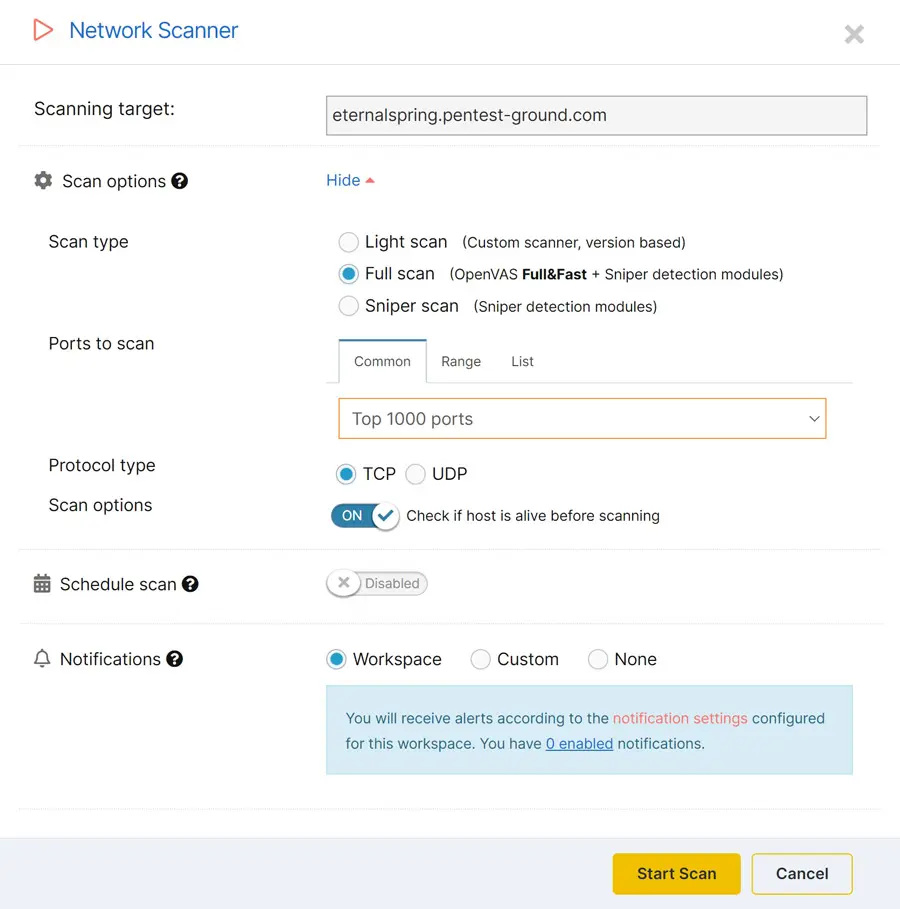
When you choose a paid plan and log into your Pentest-Tools.com account, you can select and combine the following network scanning parameters:
- Target: Option to scan a single IP address or a hostname (ex.
webmail.mydomain.com). - Scan type - Light: Uses a custom-built vulnerability scanning engine which is very fast since it uses service versions to detect vulnerabilities.
- Scan type - Full: Combines Sniper detection modules and OpenVAS for in-depth network scanning.
- Scan type - Sniper: Uses only Sniper detection modules to identify critical vulnerabilities in widely used software.
- Ports to scan - Common: Scans only OpenVAS default ports or the top 10, 100, 1000, or 5000 most common ports. When you choose this, OpenVAS default is the default scan option.
- Ports to scan - Range: Allows you to specify a range of ports to be scanned. Valid ports are between 1 and 65535.
- Ports to scan - List: Enables you to specify a comma-separated list of ports to be scanned.
- Protocol type - TCP: Tells our Network Vulnerability Scanner to only scan TCP ports.
- Protocol type - UDP: Instructs our engine to scan only UDP ports.
- Check alive: Enables the check alive mechanism before searching for any open ports during the discovery phase.
What to do after running the Network Vulnerability Scanner
Besides the Network Vulnerability Scanner, you have a full arsenal of vulnerability scanning tools on Pentest-Tools.com to carry out a thorough and effective network vulnerability assessment. You can use the dedicated SSL/TLS Scanner to discover specific SSL and TLS configuration issues or use the TCP Port scan tool and the UDP Port scanner to meticulously map your Attack Surface.
To save even more precious time, try out our ready-to-use scan templates which group multiple tools in one bundle, so you can launch them all at once. Scan templates are also customizable, or you can build your own and reuse them to fine-tune engagements and do your best work.
With your network vulnerability assessment report, you can start digging deeper and pursue the most interesting findings in it while also getting inspiration for lateral movement and ways to abuse business logic in your pentest engagements.