Password Auditor
Technical details
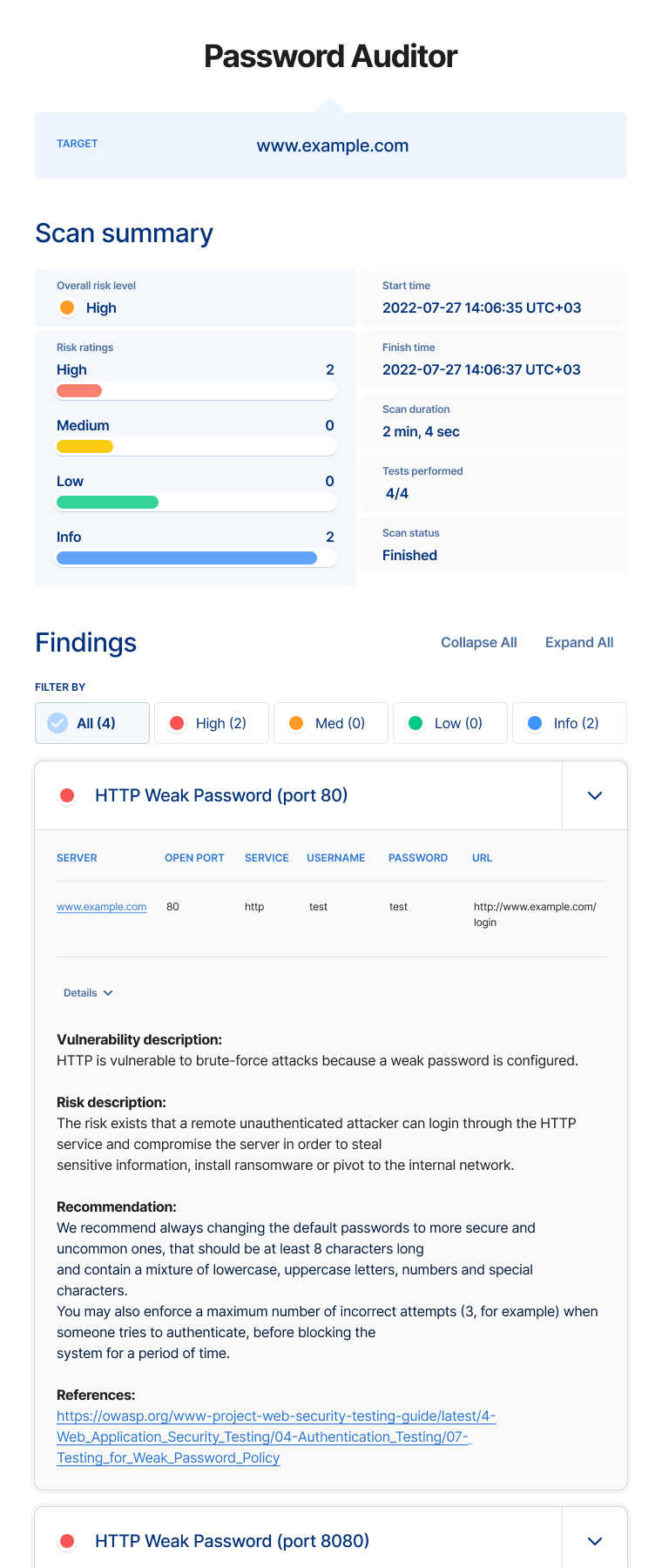
The Password Auditor is an autonomous password auditing solution for network services and web applications. It scans a URL, IP address, or hostname for network services that require authentication:
HTTP: Web forms, Basic, Digest, NTLM, RDP, SSH, Telnet, FTP, Redis, VNC, MySQL, MSSQL, PostgreSQL, WinRM, SMB, Docker, AMQP, MQTT, STOMPThe tool detects weak credentials automatically by trying to log in using the usernames and passwords from the input wordlists.
There are two default wordlists – with usernames and passwords – which you can use, but you can add as many custom ones as you need. A custom wordlist can include up to 50000 words (200 characters max. length/word) as long as it stays under 16 MB.
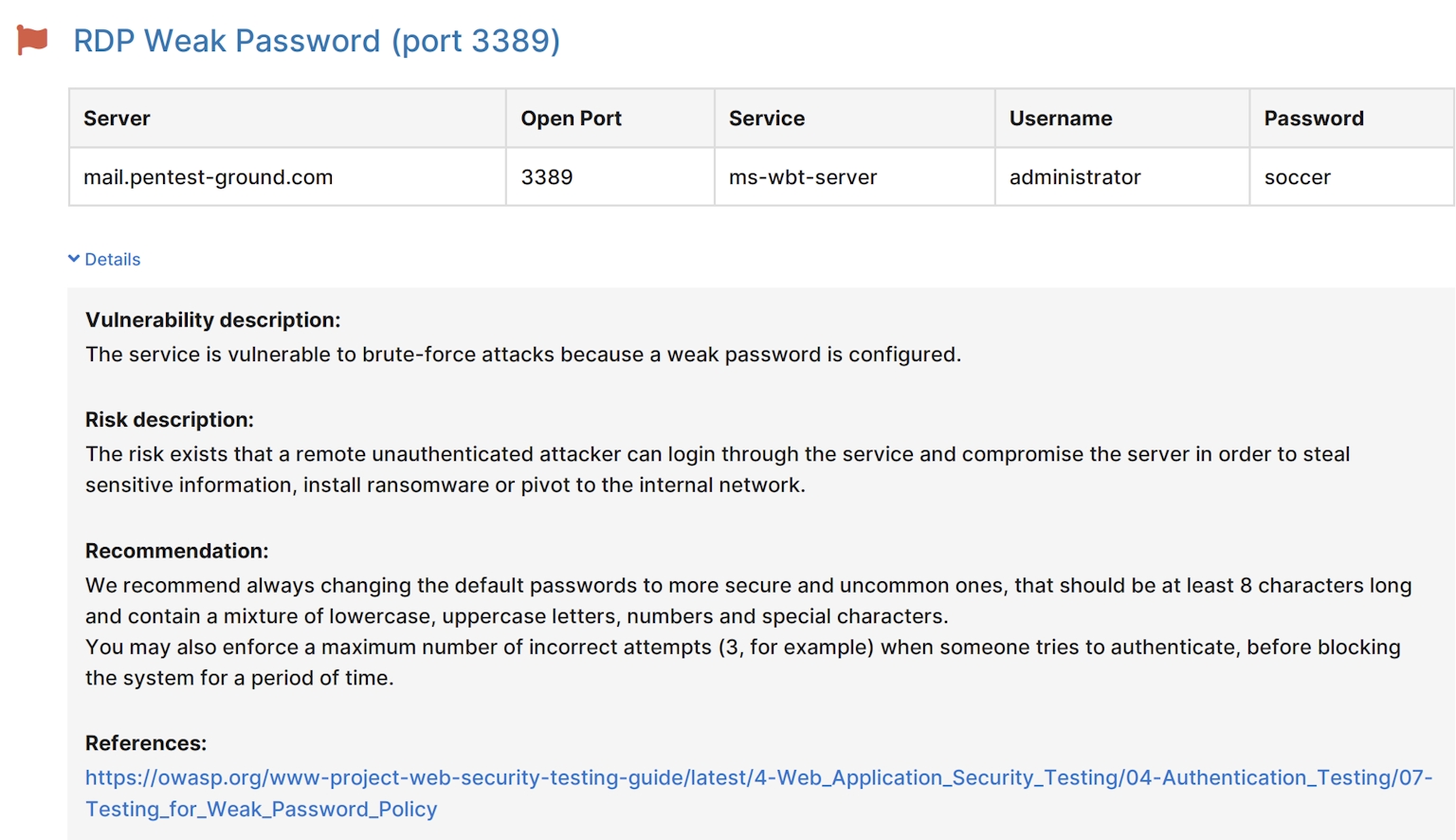
Another important functionality of our password auditing tool is the ability to test for default credentials based on the service found on a specific TCP port.
Our Password Auditor also has a unique feature: it automatically detects whether a web form authentication attempt was successful or not. This speeds up how you find weak credentials in:
- Network services: HTTP, SSH, Telnet, FTP, Redis, VNC, RDP, MySQL, MSSQL, PostgreSQL, WinRM, SMB, AMQP, MQTT, STOMPSSH, FTP, MySQL, MSSQL, PostgreSQL, RDP, etc.
- and Web interfaces: WordPress, Drupal, Sharepoint, cPanel, phpMyAdmin, etc.
The tool comes pre-loaded with a credential database for almost all frameworks and network services, which makes testing for known default/common credentials hassle-free and efficient.
The Password Auditor also correctly detects passwordless protocols (e.g. Docker API) and generates findings accordingly.
Our password auditing tool supports two types of attack:
- Dictionary attacks, where it tries all the passwords in your wordlists against a username before moving on to test the next one.
- Password Spraying attacks - where it tries every username against a password from the passwords wordlist before moving on to the next one. You can define how many attempts per period the tool runs in a time period you define, to avoid user account lockout.
Parameters
| Parameter | Description |
|---|---|
| Target | This is the URL/ IP address/hostname to scan. |
| Attack type | Choose the type of brute force attack that the Password Auditor will perform (Dictionary or Password Spraying). Default: Dictionary. |
| Ports | Choose which ports to scan for authentication services. Default: Top 100 common ports. |
| Services | Choose the services you want to audit (HTTP, SSH, FTP, Telnet, etc.). They will be automatically matched to the open ports. For example: Apache running on port 2174 will trigger the HTTP module. |
| Wordlists | Specify a custom wordlist for usernames/passwords. |
| Attempt default credentials | Try to log in with publicly known default/common credentials for each service and product. Default: enabled. |
| Delay between attempts | Time delay (in seconds) between two consecutive authentication attempts. Default: 0 (no delay enforced). The value must be an integer between 0 and 600. |
| Lockout period (Password Spray only) | Time delay (in minutes) between trying Attempts per period passwords for each username. Use this parameter to instruct the tool to wait until account lockout counters reset. Default: 5. The value must be an integer between 1 and 720. |
| Attempts per period (Password Spray only) | The number of passwords to attempt for each username in the wordlist before waiting for the Lockout period for account lockout counters to reset. Default: 2. The value must be an integer between 1 and 50000. |
How it works
The Password Auditor starts by doing a port scan and service discovery against the target system to discover which services support authentication.
It then tries common username/password combinations (from a predefined wordlist) or default credentials (from a credential database) for each service found in the previous step.
If the service is web-based, the Password Auditor uses Selenium to automatically detect the login interfaces and form parameters used for authentication. The tool is capable of determining if a web-form authentication was performed successfully or not.